You write a specific title like the above when it has happened to you. We fought them for 4 years with our client, Create Room, and they never gave up. We took down over a thousand websites through copyright violations. Sometimes we had to try a little bit harder if it was through a foreign hosting platform like Alibaba. Rather than complain I’m going to tell you how we went from 1,000 scammer Facebook ads to 0 and 250 scam websites from 326 down to 77 and getting lower.
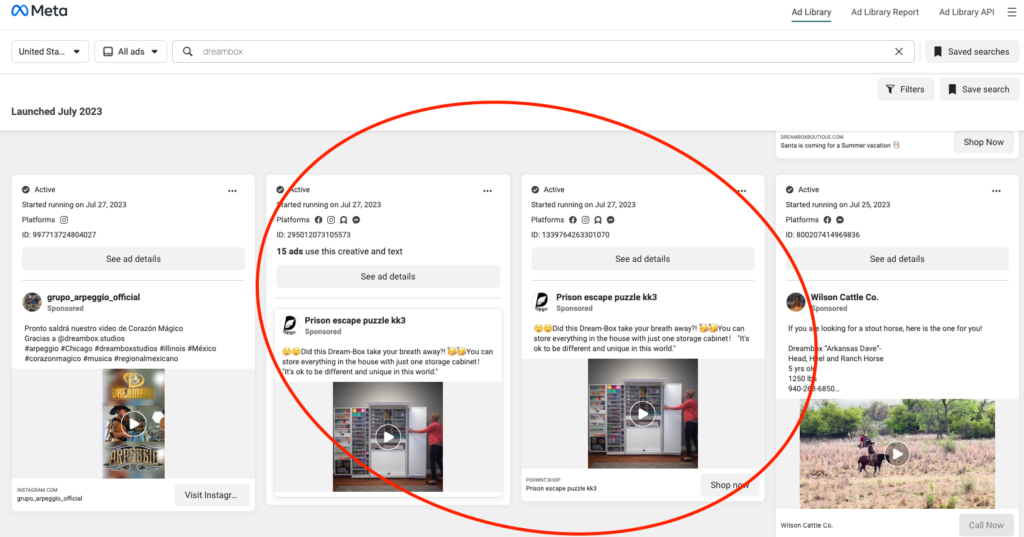
Step 1: You have to first Identify ads the scammers have live. We used Facebook Ad Library for this. Simply search for the product they are scamming. For us the Dreambox and as you can see they have 16 ads up.
Step 2: How to use Facebook or Meta Brand Rights Protection located in Ad Manager?
This software helps you report ads as a brand and from our experience they get taken down in a couple of hours vs days if you report as a consumer in the library.
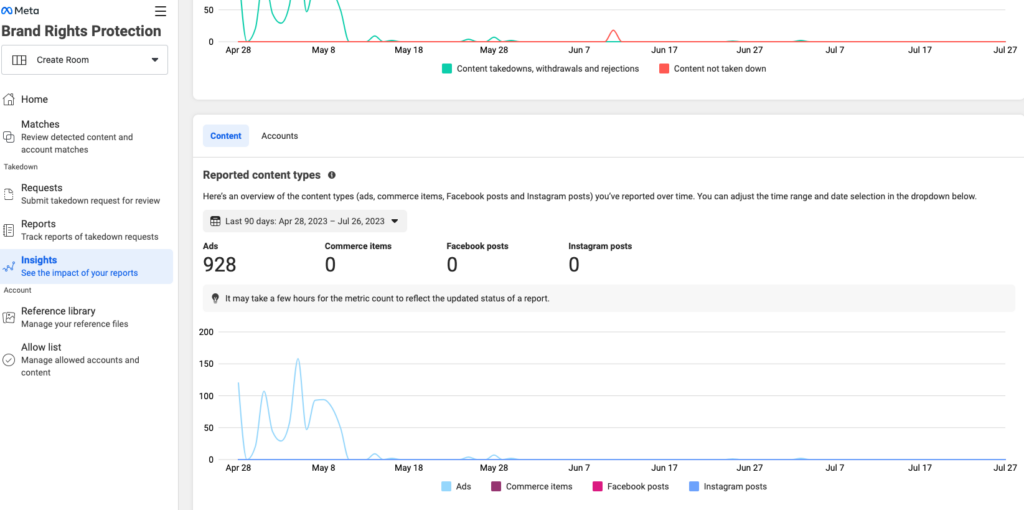
Their Reporting only goes back 90 days, but still helpful to see trends.
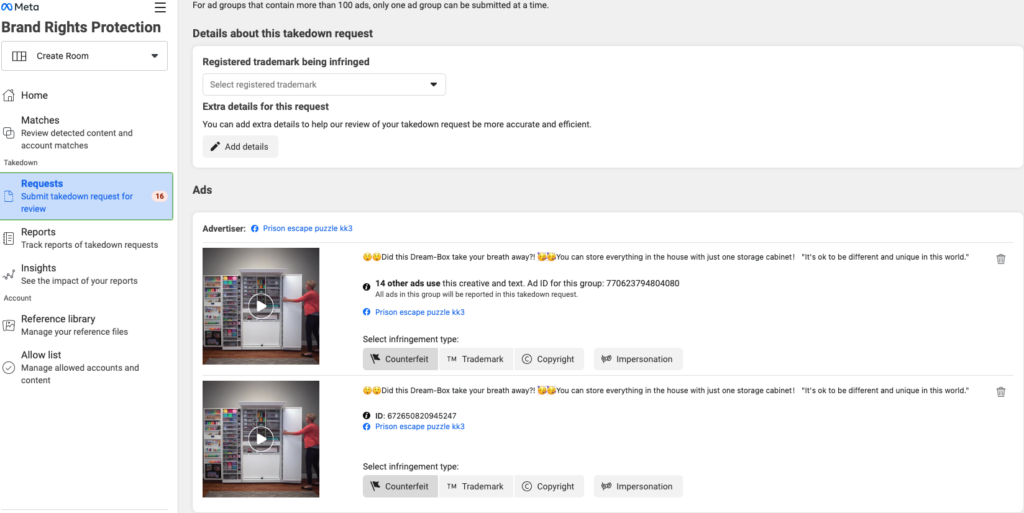
You can search for ads within this platform and report them as counterfeit, trademark, copyright, or impersonation. We marked ours as Counterfeit even though it is more fraudulent as they aren’t selling any products.
- Counterfeit: Counterfeiting refers to the act of making or selling lookalike goods or services with the intent to deceptively represent its authenticity, usually for economic gains. Counterfeit products are typically inferior in quality and are illegally branded with trademarks identical to or hard to distinguish from registered trademarks.
- Trademark Infringement: Trademark infringement is a violation of the exclusive rights attached to a registered trademark without the authorization of the trademark owner. The infringement occurs when one party, the ‘infringer’, uses a trademark that is identical or confusingly similar to a trademark owned by another party, in relation to products or services which are identical or similar to the products or services of the other party.
- Copyright Infringement: Copyright infringement involves the use, distribution, or reproduction of copyrighted works without the permission of the copyright holder. This can include copying a book, sharing music or movies online without the copyright holder’s permission, or using a copyrighted image in a blog post without proper licensing or attribution.
- Impersonation: Impersonation is an act of pretending to be another person for the purpose of entertainment or fraud. In a legal context, this can mean assuming another person’s identity with the intent to deceive or defraud others, often for personal, financial, or other gain. It can take many forms, such as identity theft, phishing, or the creation of fake profiles on social media platforms.
Websites
You are going to waste more time than you save in this endeavor unless you get the help of professionals. We used Redpoints and their software finds websites before they even cause harm to your customers. You verify it is fraud and they will take it down for you. This has saved us countless hours of time. You can see their dashboard below.
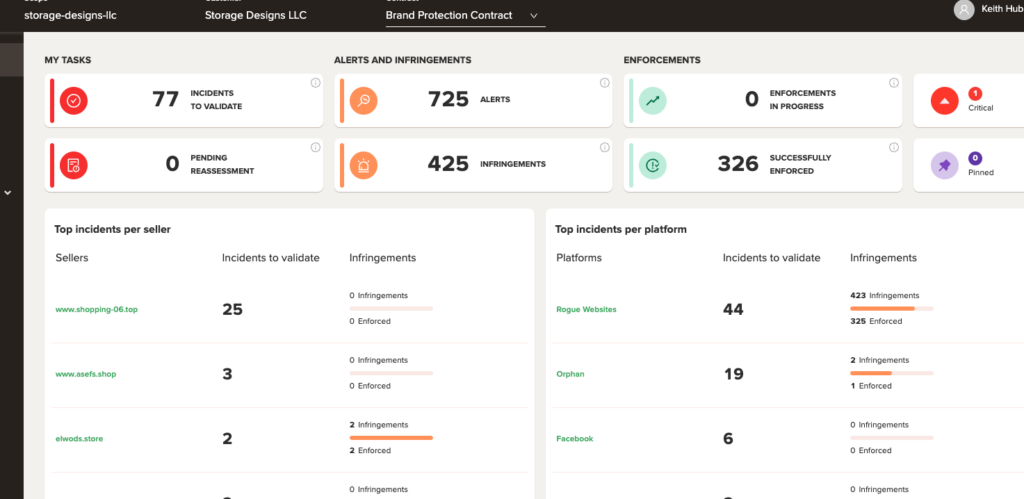
If you have questions please reach out so we can point you in the right direction. We have combated this in the past and unfortunately still in progress. The scammers aren’t giving up, but neither are we.
